Hsinchu, Taiwan – Mar 23, 2022 – Emotet first appeared in 2014. Its activity ceased in early 2021 after the takedown coordinated by Europol and Eurojust. Unfortunately, the new Emotet malware returned in November 2021 with the help of TrickBot.
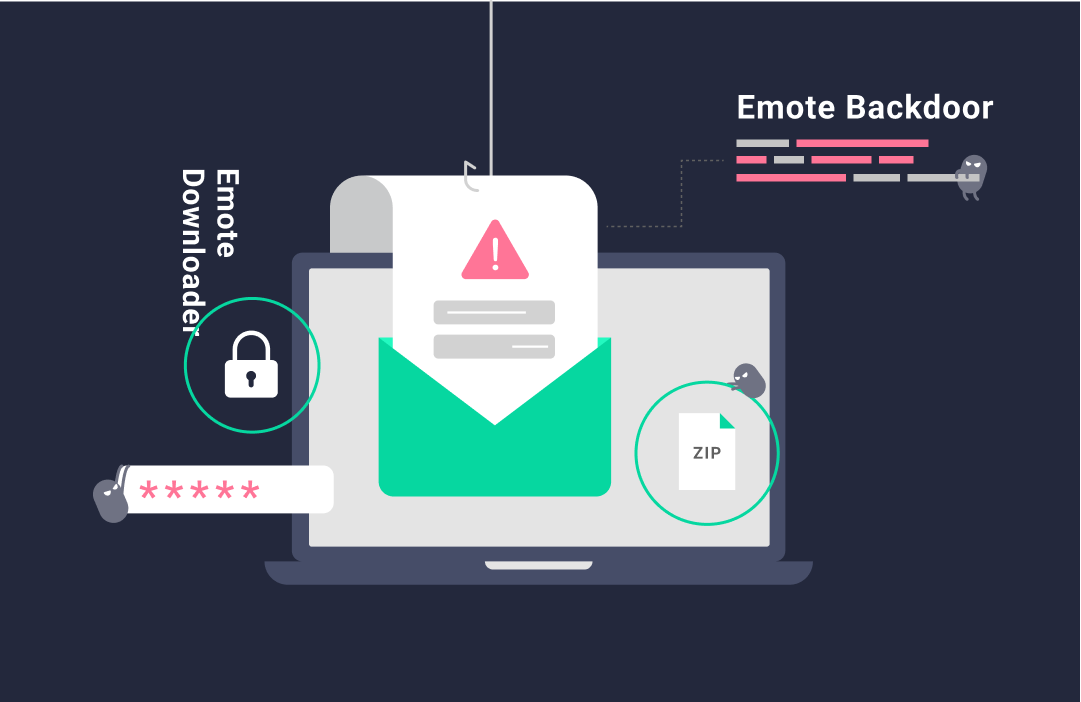
It is observed that the new Emotet malware grows steadily since then. Over 2.7 million cases of Emotet malware are detected globally so far. According to the threat analysis report of Black Lotus labs, Emotet malware is more popular in Japan, India, Indonesia, Thailand, South Africa, Mexico, United States, China, Brazil and Italy.
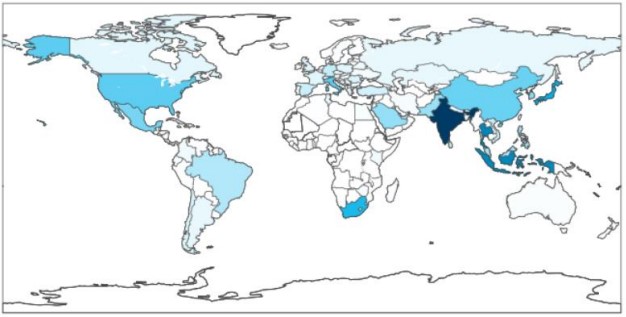
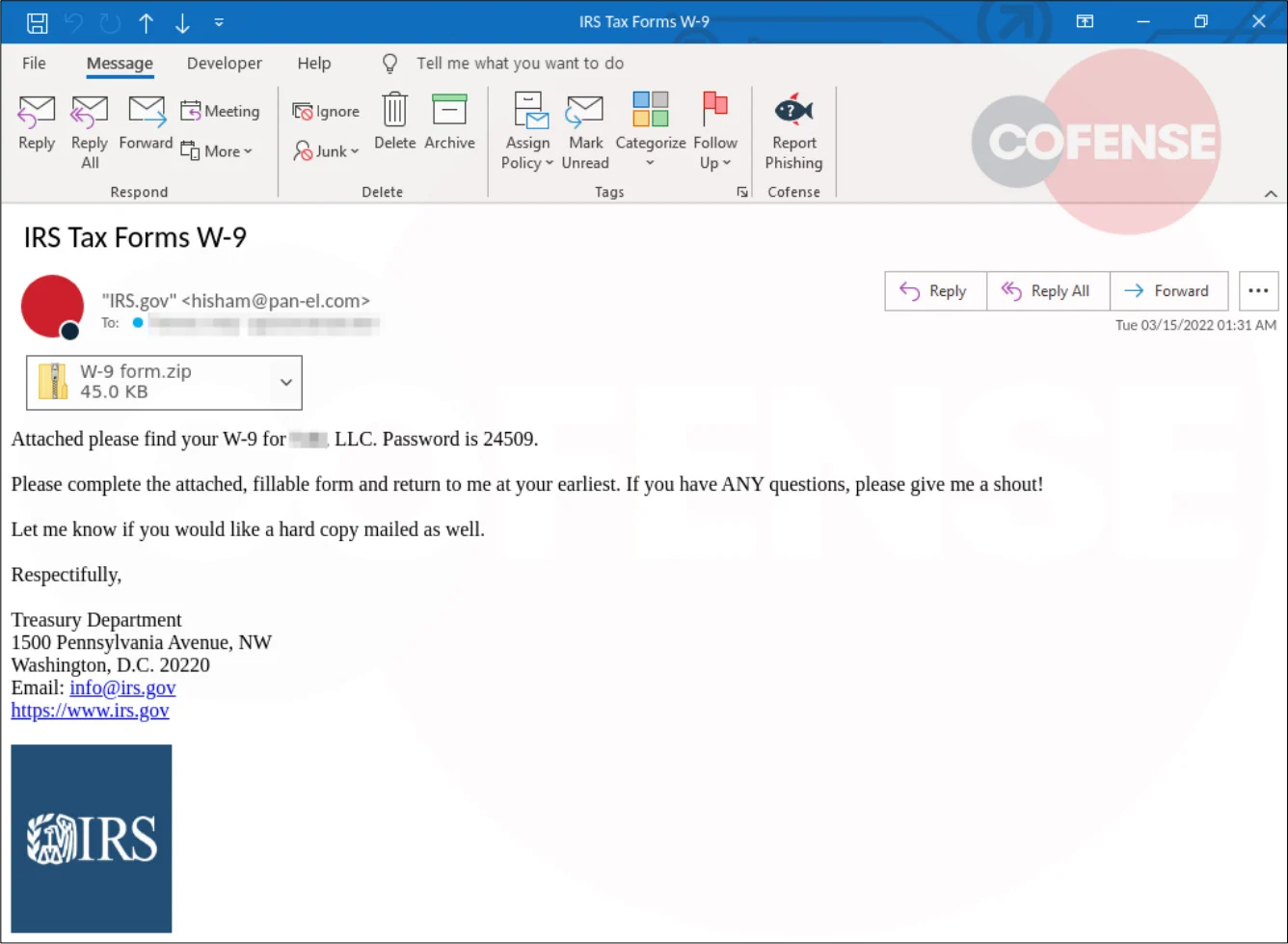
Emotet malware is sent as an email with an encrypted zip attachment. It is tax season in US currently. Multiple phishing campaigns send out Fake IRS (Internal Revenue Service) emails. Actually those fake emails are Emotet malware.
The above is the popular form of Emotet malware in US now. For the Emotet malware sample Lionic collected from Japan, the form is the password-encrypted zip with Excel file inside. And the Excel file contained malicious macros.
The Emotet Downloader Malware
As mentioned previously, Emotet malware is sent as an email with an encrypted zip attachment. The email body looks like a normal email which mentioned the password of the attached encrypted zip file.
Once users decompress the encrypted zip by using the password written in the email body, they will obtain a Microsoft Excel file usually. Most people do not aware that an Excel file is possibly to be a malware and open it.
The malicious macros inside the Excel file will download the Emotet backdoor. And then it is loaded into memory directly or by using PowerShell.
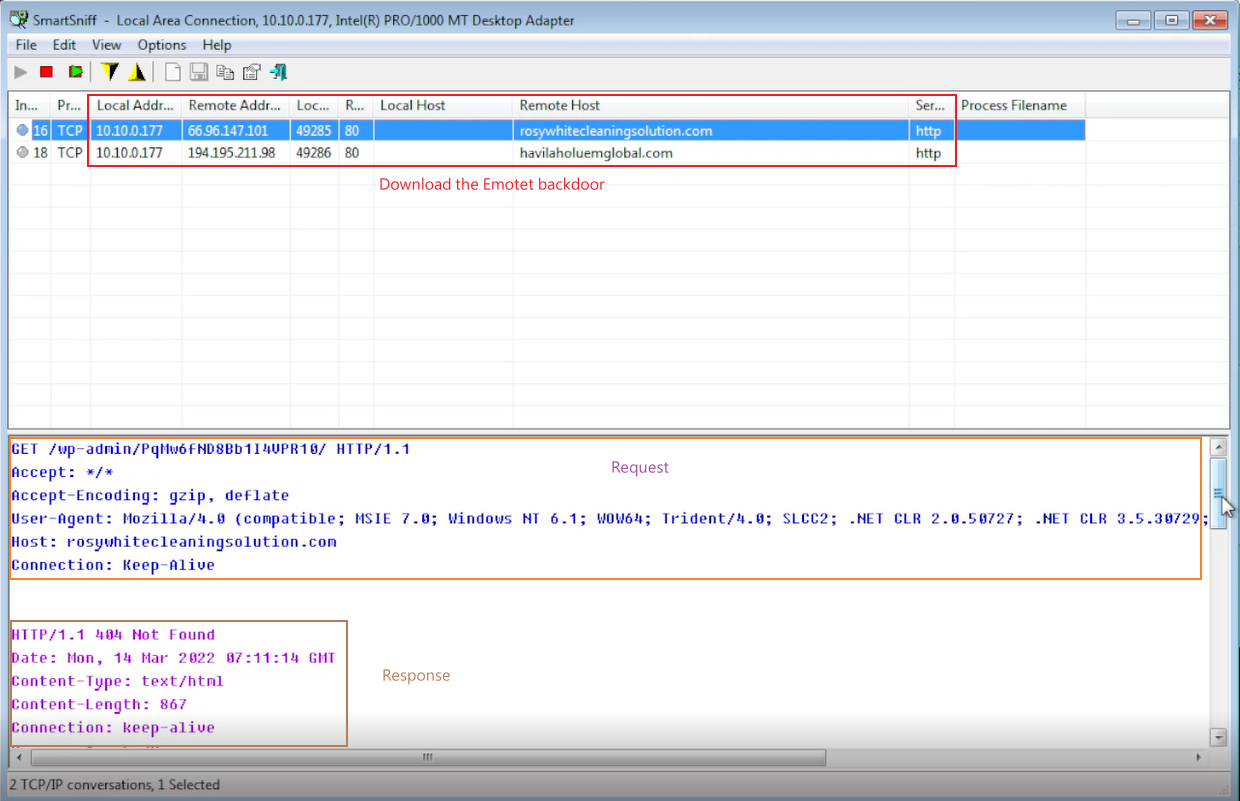
Once loaded, the Emotet backdoor will search for and steal emails to use in future phishing campaigns and drop additional payloads such as TrickBot or Qbot that commonly lead to ransomware infections.
The Actions of Lionic
No security network appliance and endpoint anti-virus programs can check an encrypted zip file because they do not know the content of the encrypted zip file. But Emotet downloader malware is hiding in encrypted zip file. Solving the Emotet malware is very challenging.
“Emotet hiding in encrypted zip is so tricky.” said Lionic security researcher Marcus Deng. “It exploits people’s habits and is hard to discern, much as Emotet forces people to play the game of Minesweeper.”
When Lionic Security Research Team received the first Emotet issue from one Japan customer, they requested us to research and design the short term solution and long term solution for solving Emotet. The short term solution should be working under the current firmware of customers’ network appliances.
Lionic Security Research Team was brainstorming together. Finally the obstacle of extracting signature from the Emotet encrypted zip file is overcome. The special Anti-Intrusion rules for blocking Emotet malware in email are implemented in several hours, although with some limitations. This is probably the best solution under the unmodified firmware. Meanwhile, Lionic members are working hard to build the long term solution involving firmware upgrade.
As we mentioned earlier, the encrypted zip file is a malicious downloader only. It will fetch the Emotet backdoor and execute. The Emotet backdoor then steals the contacts, passwords and other status.
Therefore the Anti-WebThreat feature of Lionic security technology and the related Anti-WebThreat rules database are suitable to block those Emote backdoor URLs. This is part of long term solution. So far Lionic has collected thousands of Emotet backdoor URLs. All known Emotet backdoor URLs can be blocked.
Conclusion
Pico-UTM has the Lionic Security Technology inside. It can block all known Emotet backdoor URLs now. That is, the Emotet downloader malware is blocked indirectly. At least the Emotet malware is unable to bring you any damages at this moment because the real bad guy is not downloaded.
After our long term solution is done, the complete Emote malware solution will be integrated into Pico-UTM at the first time. And then, Pico-UTM can defend against Emote malware totally. People who suffered from Emote malware can consider adopting the Pico-UTM now.
References:
- “Over 2.7 million cases of Emotet malware detected globally”, https://mainichi.jp/english/articles/20220215/p2g/00m/0bu/038000c
- “As tax deadlines approach, Emotet malware disguises itself in an IRS email”, https://www.tripwire.com/state-of-security/security-data-protection/tax-deadlines-emotet-malware-irs-email/
- “Here are the new Emotet spam campaigns hitting mailboxes worldwide”, https://www.bleepingcomputer.com/news/security/here-are-the-new-emotet-spam-campaigns-hitting-mailboxes-worldwide/
- “Emotet growing slowly but steadily since November resurgence”, https://www.bleepingcomputer.com/news/security/emotet-growing-slowly-but-steadily-since-november-resurgence/
關於Lionic Corporation
Lionic Corporation是創新的「深層數據包檢測」解決方案的全球供應商。 Lionic的技術包括完整的基於DPI的軟件引擎和相關的管理軟件,這些軟件提供可解決防病毒,防入侵,防網絡威脅的「安全解決方案」。 以及「內容管理解決方案」,用於解決應用程序標識,設備標識,基於應用程序的QoS,Web內容過濾,家長控制。
Lionic的安全和內容管理解決方案,基於雲的掃描服務和簽名訂閱服務已經在世界範圍內廣泛部署, 他們幫助服務供應商,網絡設備製造商,半導體公司等,以實現下一代家用商業路由器網關,SD WAN邊緣和雲網關,高級防火牆,UTM,智慧網卡和移動設備。 那些由Lionic支持的產品可提供更好的網絡管理和保護全球網絡免受不斷增加的安全威脅。