Hsinchu, Taiwan – Jan 30, 2022 – Last week, Conti ransomware hits Delta Electronics, a tech giant which supplies Apple, Tesla, HP, Dell and other big companies in the world. The headquarter of Delta Electronics is located in Taiwan. Some reports mentioned that 1,500 servers and 12,000 personal computers are impacted. And a USD 15 million ransom is asked. However, Delta Electronics denied it via the announcement system of Taiwan Stock Exchange. The Taiwan branches of Microsoft and TrendMicro are invited to investigate this ransomware event.
The screenshot from Delta Electronics official website.
Conti Ransomware
Conti is a sophisticated Ransomware-as-a-Service (RaaS) model first detected in December 2019. It grows rapidly and get beyond other RaaS like Ryuk. The Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI) and National Security Agency (NSA) issued a warning together about Conti in Sept 2021,
The infection of Conti ransomware begins from a lot of phishing emails. Once a user open the malicious attachments, Conti ransomware is executed and uses several vulnerabilities to infect other computers - MS17-010, CVE-2021-34527 and CVE-2020-1472. And MS17-010 includes CVE-2017-0143, CVE-2017-0144, CVE-2017-0145 and CVE-2017-0146.
| Id | Description | CVSS v3 Score | Severity Level |
|---|---|---|---|
| MS17-010 | Several vulnerabilities could allow remote code execution if an attacker sends specially crafted messages to a Microsoft Server Message Block 1.0 (SMBv1) server. | N/A | N/A |
| CVE-2021-34527 | Windows Print Spooler Remote Code Execution Vulnerability | 8.8 | High |
| CVE-2020-1472 | An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’. | 10 | Critical |
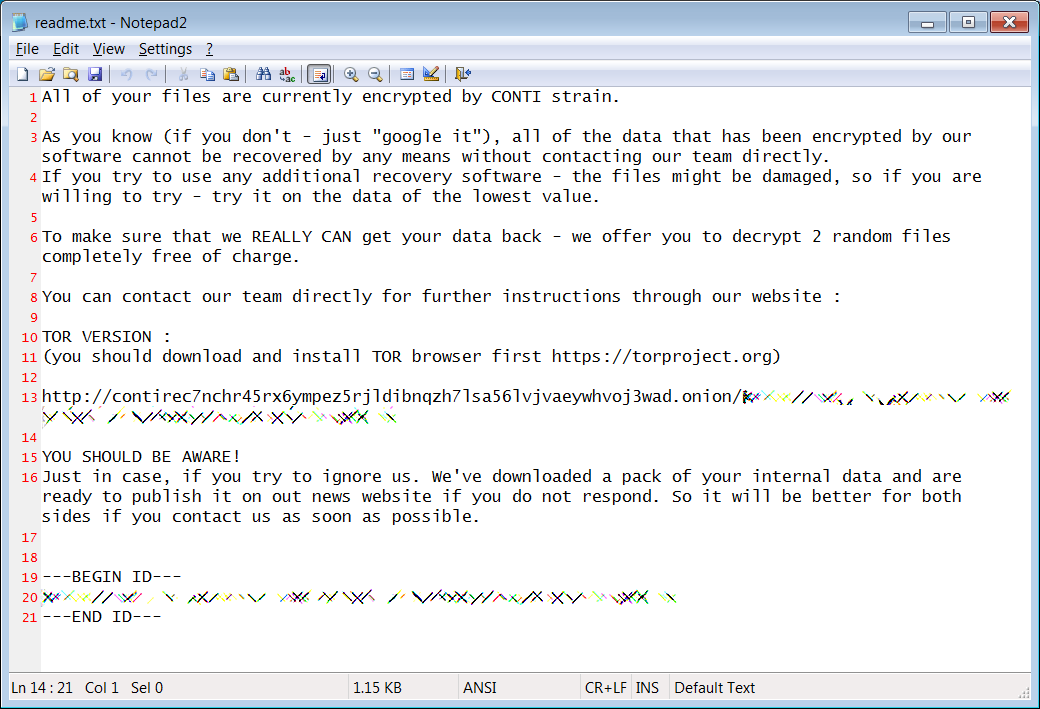
Therefore, 1,500 servers and 12,000 personal computers of Delta Electronics are infected. Most files on those computers are encrypted by AES-256 with a key only known by Conti ransomware gang. The Conti ransomware gang asked Delta Electronics to pay a USD 15 million ransom for a decryptor and stop leaking files stolen from its network.
Lionic Security Team
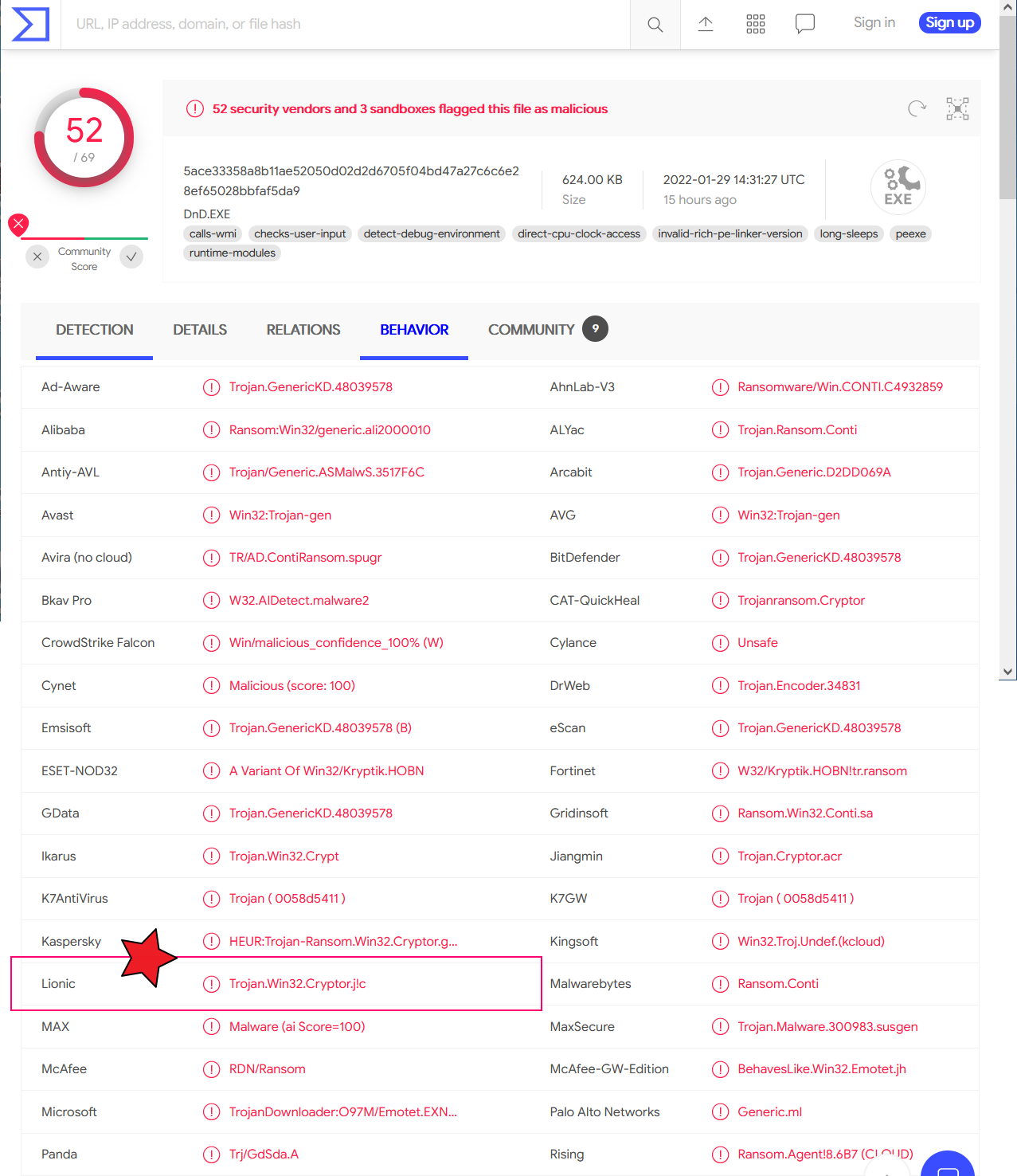
CTWANT media reported that the hash value of Conti ransomware in this event is
5ace33358a8b11ae52050d02d2d6705f04bd47a27c6c6e28ef65028bbfaf5da9. Lionic has collected several millions of ransomwares so far. The Conti ransomware family is in our collection already and includes the above one exactly.
Detecting all the several millions of ransomwares can be done via the Lionic Anti-virus Cloud Service. All Lionic security technology based products can protect against Conti ransomware if its Lionic Anti-virus Cloud feature is enabled. Lionic Pico-UTM can block this malware, of course.
Conclusion
Delta Electronics is a tech giant in the world and has many resources. There may be some reasons caused such tech giant to has so many computers which are not updated to latest version. They may think their servers and personal computers are in a closed network and thus their computers may not be modified once they are working. It is wrong because most ransomware outbreak inside LAN.
In this situation, the IT guys of Delta Electronics can use the Lionic Pico-UTM as the “Virtual Bug Fix”. They can deploy a large volume of Pico-UTM in many important nodes of their LAN. All the nodes which installed Pico-UTM can filter out the malicious content bidirectionally including Conti ransomware. The more Pico-UTM are adopted, the impact of ransomware is less. And then IT guys do not need to worry about the ransomware or any unsolved vulnerabilities. Lionic Pico-UTM is cost effective and therefore is suitable to deploy a large volume.
References:
- The first Taiwan media reports this event - “獨家/台達電被駭遭勒索4.1億元 估約1.35萬台電腦被加密”, https://www.ctwant.com/article/165246
- Taiwanese Apple and Tesla contractor hit by Conti ransomware, https://www.bleepingcomputer.com/news/security/taiwanese-apple-and-tesla-contractor-hit-by-conti-ransomware/
- Alert (AA21-265A) Conti Ransomware, https://www.cisa.gov/uscert/ncas/alerts/aa21-265a
- “CISA, FBI, and NSA Release Joint Cybersecurity Advisory on Conti Ransomware”, https://www.cisa.gov/uscert/ncas/current-activity/2021/09/22/cisa-fbi-and-nsa-release-joint-cybersecurity-advisory-conti
- Conti Ransomware, https://blog.qualys.com/vulnerabilities-threat-research/2021/11/18/conti-ransomware
關於Lionic Corporation
Lionic Corporation是創新的「深層數據包檢測」解決方案的全球供應商。 Lionic的技術包括完整的基於DPI的軟件引擎和相關的管理軟件,這些軟件提供可解決防病毒,防入侵,防網絡威脅的「安全解決方案」。 以及「內容管理解決方案」,用於解決應用程序標識,設備標識,基於應用程序的QoS,Web內容過濾,家長控制。
Lionic的安全和內容管理解決方案,基於雲的掃描服務和簽名訂閱服務已經在世界範圍內廣泛部署, 他們幫助服務供應商,網絡設備製造商,半導體公司等,以實現下一代家用商業路由器網關,SD WAN邊緣和雲網關,高級防火牆,UTM,智慧網卡和移動設備。 那些由Lionic支持的產品可提供更好的網絡管理和保護全球網絡免受不斷增加的安全威脅。
